It seems like there’s a new headline every week about a big security breach or ransomware attack that has exposed sensitive data or crippled a company’s operations — further proving the case for embedding security into every aspect of your business.
Still, too many organizations are rolling the dice, betting that their complicated mix of legacy solutions with security add-ons will protect them from malware and cyberattacks. Today’s enterprise environments have become so complex and the data has grown exponentially, relying on old backup and restore solutions is no longer a safe bet. And while some new products have entered the scene for smaller businesses and workloads, options for comprehensive coverage at scale are limited.
To truly prevent malicious acts, security can’t be an add-on or an afterthought. It takes containment by design. That is, consciously bringing security into every layer of the infrastructure with maximum simplicity while drawing a secure perimeter around your data protection, making it nearly impossible for all but a chosen few to access it.
That was the impetus for founding Cobalt Iron. Our Compass® SaaS-based enterprise data protection architecture makes it possible for all enterprises to apply containment by design and to control it all through one simple interface.
We asked Cobalt Iron Chief Technology Officer Rob Marett to explain this approach and why it’s so important:
What problems were you seeing that led you to turn software-driven solutions into architecture with security at its core?
After consulting with large enterprises for many years about their data protection infrastructures, we saw that many data and IT pros were burdened with operating and maintaining overly complex and outdated data protection technologies — cobbled-together backup infrastructure that has evolved over many years with legacy backup products. These operators and engineers must maintain the operating system, the compute, the storage, the backup catalog, and the backup applications themselves — and not just one, but many, because they often use different backup products for different applications. This team was also in charge of the duct tape and baling wire that was needed to get all of it to work together. They were focusing so much time on just making it work that security was an afterthought even a burdensome barrier to getting the overloaded work done. That opens the enterprise up to all sorts of exposures.
So, as they look to replace or modernize their infrastructure, they're really looking for something that is secure, simple, and automated. That way they can sleep better at night knowing it’s working without having to fight with it.
And so Cobalt Iron was born.
Why was this the direction you took when developing Compass?
We had experienced all the challenges people were having, so we knew that Cobalt Iron's products had to be built on a secure core, with none of the duct tape and baling wire referenced earlier. It had to be a departure from existing solutions – not another layer, not another appliance.
We also knew that we would be working with large enterprises that were growing into public cloud footprints, where security was at the forefront. So, while we had to be focused on security, we also had other goals, like simplicity, automation, and analytics, which fortify the solution and make it even more secure.
For example, with Compass, enterprises don't have to keep the operating system current or do any application updates. That's all engineered and managed by software in the Cobalt Iron and Compass landscape. Automation adds to the simplicity because we have computers, rather than people, doing the work automatically and adjusting as needed. Think about it. The more people you have working inside the system, the less secure it is.
How does the team consider security during product development?
There are several security considerations during the development life cycle. The first is whether a change to the product, such as a new feature, is inherently insecure. If so, do we have to toss it out, or can we tweak it to make it secure? For example, we have avoided embedding various technologies that might introduce security vulnerabilities that don’t exist with Compass today. We've had excellent suggestions for certain new features, that once we refactored to eliminate any security weaknesses, the benefits were lost.
From there we work through the industry-standard security frameworks and use best practices for encryption authentications and hardening of systems and infrastructure. We also have a security team that meets about new features and products. Essentially, we put our hacker hats on, brainstorming all of the attack vectors that someone with malicious intent could exploit and deciding what changes we need to make to counteract any weaknesses. Finally, we firm everything up and make sure it's secure before the development begins.
What does containment by design mean to you?
Containment by design means there’s a secured perimeter around the entire backup infrastructure —traditionally a variety of products, integrations, data stores, and processes — to minimize exposure to malicious attacks. It creates as few paths as possible for an attacker to get into the solution and into your data. That's containment.
Containment is at Compass’ core. That’s why our Compass Accelerators — the systems enterprises send data to and retrieve data from for backup, archive, retrieve, and restore events — are completely isolated from a customer's network except for one single port. And that port is used for pushing and pulling data to protect.
Other than that, there's Zero Access™ to the backup infrastructure at any level. Even if someone did happen to get into the network, they can only access that one port, and it’s not something that could be attacked easily — you can't SSH into it, you can't get to a command prompt, you cannot add software, etc.
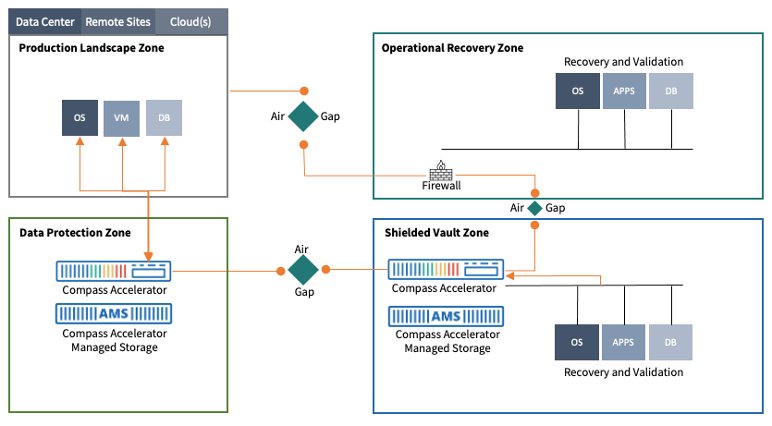 Cobalt Iron Compass delivers containment by design with multiple, isolated, immutable, and inaccessible security zones.
Cobalt Iron Compass delivers containment by design with multiple, isolated, immutable, and inaccessible security zones.
How does that compare to other data protection solutions out there?
Containment by design is a huge differentiator for Compass. Some of the newer solutions are working in these areas, but most of our competitors, especially makers of the legacy products people are using today — place a lot of responsibility on humans to configure and maintain the servers the software is running on. We just don't have that. It's all done by our Analytics Engine and the Compass landscape.
What should enterprise data managers be thinking about from a cybersecurity perspective, and where are they falling short?
What enterprises really need to be thinking about is this: "Are my data and my data protection environment secure? And can I restore them in the event that an attack happens?" That means having the right solutions, the right security, the right controls, and the right monitoring in place.
Security should not be an add-on. It should be a comprehensive strategy and the foundation of whatever data protection product they’re considering. Other backup products on the market today just weren’t built with that security focus.
And where are they falling short? Traditionally, backup is just an afterthought. It's also complex and difficult. At the same time, it's the biggest application in the enterprise because it touches everything. So it should not be an afterthought.
We’re seeing many organizations running a patchwork of older, legacy backup products and even newer products that are difficult to maintain. And while it might have worked well in the past, it's long outdated for today's climate. That's where Compass transforms things for the business. Compass doesn’t just provide new icons, new versions, or new features, but a complete modernization with a secured data protection solution.
More information about securing your data protection environment
For an independent analyst report on Compass’ security features and how it keeps your data on lockdown, download the ESG Technical Review
< Back to Blog