One need only glance at the news on any given day to see that security breaches and ransomware attacks are on the rise all over the world ... and the threats are only getting more sophisticated. If you haven’t already heeded the warnings to get your house in order, the clock is ticking.
The threat is real, ever-present, and growing. And backups are a No. 1 target because of their role as the critical last line of defense for an organization.
The financial cost of a ransomware attack can be extremely high. In fact, a 2021 Ponemon Institute report put the average cost of a data breach in 2021 at $4.24 million. That cost, coupled with the risk to public relations and customer trust, organizations can’t afford to look the other way. That’s why risk mitigation and security are rightfully at the top of every IT leader’s list of issues to solve for.
In our conversations with IT leaders, they’re asking some important questions:
- "Is our environment secure?"
- "Are we cyber resilient?"
- "Are we ready to recover?"
- "And could we recover our data cleanly?"
Another question worth asking is this: Have we locked down all of our attack vectors?
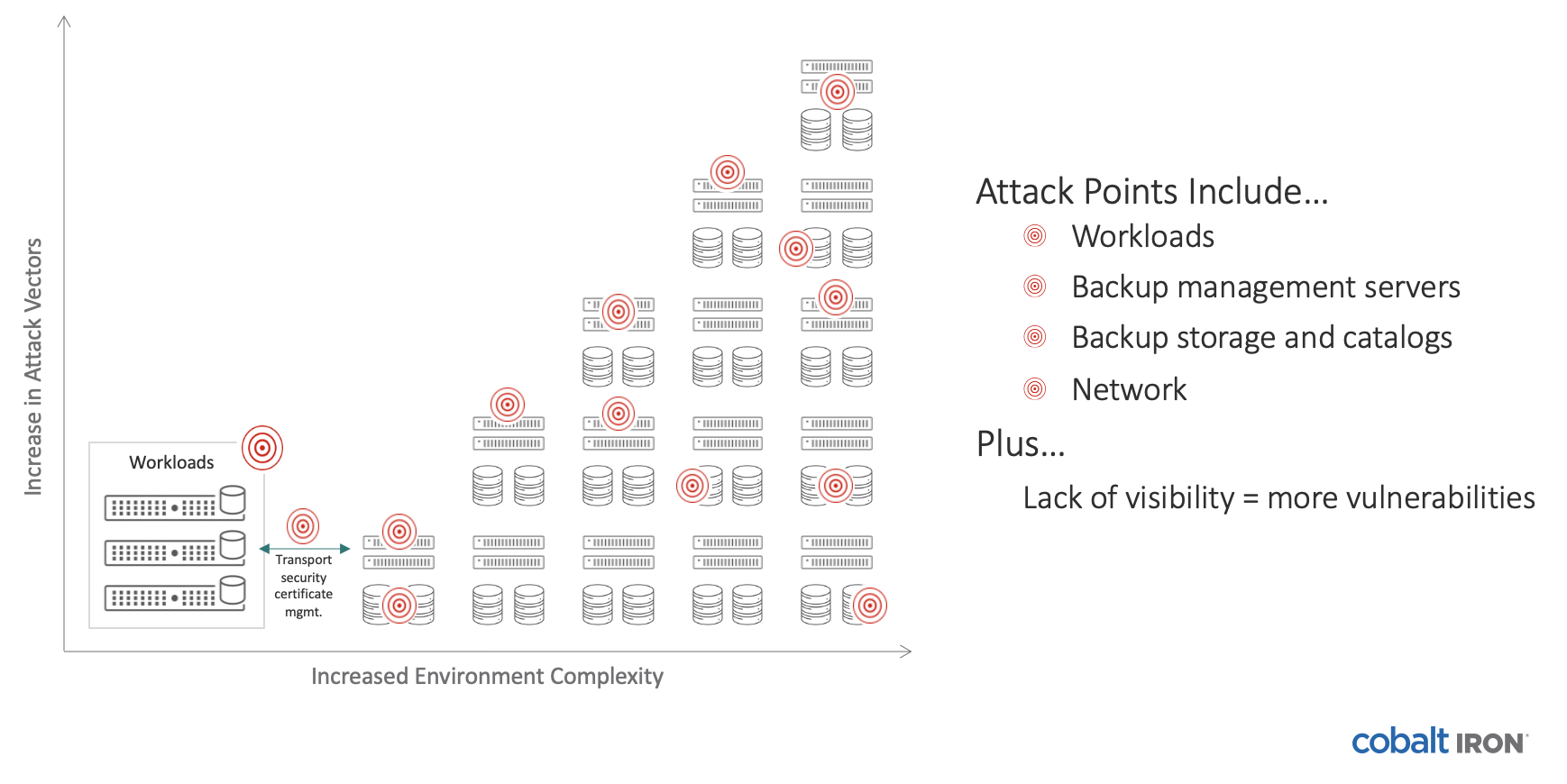
A typical large organization has a complex backup infrastructure comprising multiple, stitched-together hardware and software products that lack scalability. As the amount of backup data increases, the infrastructure grows larger and more complex ... resulting in exponentially more ransomware vulnerabilities with each new addition to the environment.
The number of attack vectors grows with your data
Common areas that are ripe for attack are out-of-date software, databases, networks, and remote sites, among many others. Most of the vulnerable attack points are either flying under the radar for a lot of companies or are too challenging to keep up with across the entire environment.
A genuinely secure backup solution will cover all potential attack points:
- Out-of-date software
- Operating systems
- Internal threats
- Applications
- Processes
- Networks
- Systems
- Storage
- Databases
- Remote sites
- Backup catalog
 Right now you might be thinking, “I’m covered because I have immutable backup storage.”
Right now you might be thinking, “I’m covered because I have immutable backup storage.”
But don’t let that lull you into a false sense of security. The truth is, most backup products today only cover about four or five of those vulnerabilities at most, leaving other components vulnerable to attack.
Immutable storage isn’t enough. To be truly secure, you need isolated zones of cyber protection and recovery to eliminate all attack vectors. One way to do that is by not allowing any access into the infrastructure at all.
This concept is called containment by design. It means there’s a secured perimeter around the entire backup infrastructure — traditionally a variety of products, integrations, data stores, and processes — to minimize exposure to malicious attacks. It creates as few paths as possible for an attacker to get into the solution and into your data.
A backup solution that takes the containment approach offers these capabilities:
- Zero Access™ to backup hardware and software components or backup data
- Multiple, automatically managed copies of backup data, including off-site
- Multiple, isolated security zones
- Data always locked down within your security access zones
- Multiple zones of air gap
- Robust authentication — including multi-factor authentication to the solution dashboard for visibility and management — without granting access to backup components or backup data
- Cyberattack event recovery and validation
... and many, many more.
Cobalt Iron Compass covers nearly all attack points. The unique Compass architecture — through its inherent inaccessibility — shields the entire landscape. Every Compass deployment includes Cyber Shield technology at no extra cost. Cyber Shield’s containment-by-design architecture locks out hackers with isolated zones of cyber protection and safe recovery. It completely eliminates common attack vectors with zero direct access to the protection zones, and it eliminates the simple but real threat of daily human errors with an analytics-driven, software-automated framework. Cobalt Iron is constantly developing enhanced security features that, when available, get pushed into your deployment at no additional cost.
So what about you? Do you have any of those vulnerabilities in your environment? Could your entire backup landscape stand up to a cyberattack? Don’t take any chances. Check out this solution brief to find out more about how Cobalt Iron Compass will protect your enterprise.
< Back to Blog